Role-based access control (RBAC) is a technique that limits access to a resource based on users’ responsibilities within an organization. RBAC ensures that users access only the resources and information relevant to their work. It is based on roles and their associated rights. Employee roles closely align with RBAC roles, and users receive privileges only to access resources permitted for a specific role.
Advantages of RBAC:
- Transparency: Roles determine permissions, ensuring that employees in the same function have the same set of rights.
- Flexibility: When an employee’s position within a company changes, it is easy to reassign them to the new role and remove the previous one.
- Security: Permissions are granted based on the principle of least privilege.
- Efficiency: Managing users and roles requires less effort, making it simpler to monitor permissions.
Principle of Least Privilege
The principle of least privilege, a core concept in information security, states that each entity should only have access to the data and resources necessary to complete its assigned tasks.
ClickHouse RBAC
ClickHouse implements RBAC to facilitate access control management. The key components of ClickHouse RBAC are:
- User Accounts: Identify specific end users or applications that connect to ClickHouse and access data.
- Roles: Define users’ privileges, settings, and limitations.
- Settings Profiles: A group of settings applied to a role or user.
- Quotas: Restrict the amount of resources a role or user can consume over a given period.
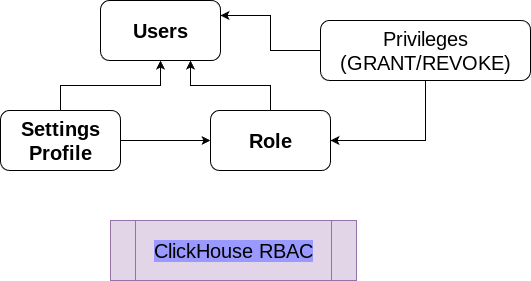
The relationships between these access entities and their assignments are depicted in the above illustration. Within ClickHouse, you can:
- Assign roles, settings profiles, and specific privileges to users.
- Grant roles access to settings profiles and particular privileges.
Although this method helps implement RBAC, the database administrator must enforce the Principle of Least Privilege. For example, even if two users, A and B, share the same role, they may have different privileges due to individually assigned settings profiles and specific privileges. To maintain consistency and strictly follow the Principle of Least Privilege, we should adopt the following RBAC strategy.
Best Practices
- Assign roles to users rather than granting privileges directly.
- Grant privileges and apply profile settings to roles instead of individual users.
This approach is more straightforward and efficient, ensuring uniform privilege management and strict adherence to the Principle of Least Privilege.
References
https://clickhouse.com/docs/en/operations/access-rights
https://kb.altinity.com/altinity-kb-setup-and-maintenance/rbac
Photo by Pixabay: https://www.pexels.com/photo/gold-colored-abus-padlock-with-key-39624/

